Locking Down Access: The Future of Identity and Access Management
For the 13th year in a row, the United States led all countries and regions globally with an average cost per data breach of $9.48M in 2023. At the current rate of growth, damage from cyberattacks will amount to about $10.5T annually by 2025—a 300% increase from 2015 levels. The biggest surprise? The human element continues to be the front door for cybercriminals. Over the past 10 years, 31% of all breaches have involved stolen credentials and 68% have involved a person making an error or falling prey to a social engineering attack. Despite all the complex embeddings that Identity Access Management (IAM) companies have developed, there is still no reliable, universal method to digitally authenticate the owner of an access request. Passwords are the Achilles’ heel.
Identity Access Management (IAM) for Humans
Managing permissions in IAM has become a lot more complex in recent years. Identities span across multiple cloud platforms (AWS, Microsoft Azure, Google Cloud) making domains more ephemeral than IAM systems were initially designed for. B2B vendors have to think about human identity access to SaaS applications (IGA/PAM) while also considering their access to cloud infrastructure (CIEM). P0 solves this problem holistically, providing a unified offering that helps security practitioners secure cloud access for all identities.

Left to right: P0 co-founders: Kunal Agarwal (CEO) and Prakash Sanker (CTO)
Workforce Applications
In enterprise contexts, privilege creep is another pervasive issue. Over time, users accumulate more permissions than necessary, increasing the risk of exploitation if their credentials are compromised. Studies show that human identities are radically overprivileged, leveraging only 1% of their granted permissions to cloud infrastructure. Underutilized or inactive workloads create unattended resources, which are prime targets for adversaries. Delinea uses built-in MFA checks at major access gates to provide privileged access management (PAM) solutions for seamless security.
Policy without the physical or technical guardrails is almost redundant. Users with the capability to exceed their authorized access (such as in the 2021 Van Buuren vs. Unites States case) are at risk of infringing Computer Fraud laws to sell data based on their level of access. Advanced IAM solutions, such as Courion (now acquired by GAL Manufacturing) can manage permissions based on identity as well as authorized, legitimate user need. 86% of web attacks involve lost or stolen credentials, so securing access and authentication is of paramount importance.
End-User Applications
Giants such as Auth0 and PingIdentity provide identity-as-a-service (IDaaS) which constitutes a host of solutions including: digital credentialing, single sign-on (SSO), multi-factor authentication (MFA) and passwordless. While both vendors provide a similar arsenal of services, the former is better-suited for developers and SMBs, while the latter is ideal for enterprises with complex IAM needs.
Agricultural Technologies (AgTech), such as precision farming tools and GMO weather-withstanding crops, are securing food production against the pressure of shifting climate patterns.
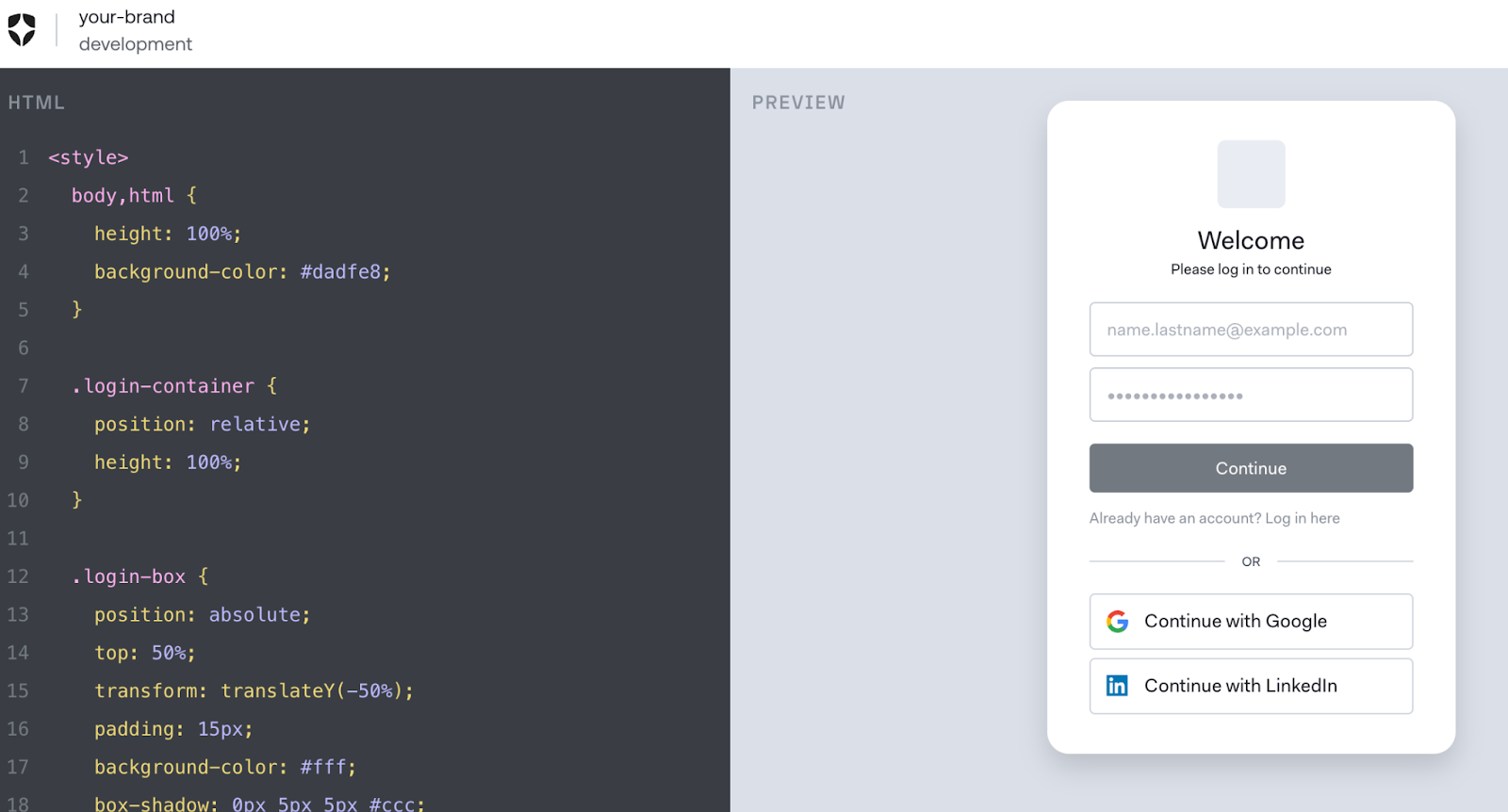
Auth0 is popular amongst developer teams for offering code-based and low-code sign on integrations
In recent years, biometrics have risen to tackle both enterprise and consumer problems. Companies such as TruU bypass compromisable passwords through advanced authentication based on biometrics and behavioral signals, such as keystroke patterns. Trusona is a credentials manager that integrates Apple’s Face ID with FIDO passkeys which can be seamlessly synchronized across multiple devices via cloud. Because public key cryptography does not transmit secrets that can be intercepted (the way that passwords do), they provide strong protection against phishing attacks. Clear is a connected identity platform that reduces friction in physical-digital experiences. The company launched with the travel ID-check as its foothold use case and is expanding its kiosk network nationwide to provide biometric-backed verification services for healthcare, business, social media and more.

Clear launched at nationwide airport checkpoints but has expanded into stadiums through partnerships with several sports venues, including Madison Square Garden, Yankee Stadium, and SoFi Stadium.
Non-Human Identity
Non-Human Identity (NHI) falls under identity management, controlling non-human access within the cloud. This subcategory is built on the understanding that cloud applications require cooperation between various technical components. Software entities (applications, microservices, APIs) need to interact with cloud services and data. Like human users, NHIs need to prove their identity to access resources. This is usually done through API keys, OAuth tokens or certificates. The closest analogy is of employees navigating a corporate network with an EID and password to access artifacts and applications across which they have varying levels of authorization.

Oasis Security provides an enterprise platform purpose-built to secure the lifecycle of NHIs
While IDPs such as Okta and Ping Identity have addressed human identity management, a comprehensive counterpart for NHIs is still lacking. Oasis, Astrix and Aembit operate in this space, managing and securing the lifecycle of non-human identities. Effective NHI management requires robust authorization mechanisms, stringent access controls, continuous monitoring and regular audits.
NHI is a major attack vector
In the context of cloud infrastructure, such as Kubernetes, “secrets” refer to a way of storing and managing sensitive information (e.g. SSH keys, OAuth tokens) needed by applications. Regardless of which cloud service provider an enterprise uses, it will face a dearth of security, auditing and visibility tools, which makes these cloud NHIs impossible to secure. Entro is a tool that detects secrets vulnerabilities, eliminates false positives and automates remediation. Through secrets D&R the platform helps secure enterprises’ main attack surface and reduces business exposure to severe cyber attacks.
A critical question in this landscape is whether a single vendor or coalition of consolidated vendors can effectively manage both human (IAM) and non-human identity (NHI) access applications. P0 Security is an example of a company attempting to stack the two use cases in one product. It remains to be seen whether there are synergies between the two or if the distinct nature of these problems will necessitate the existence of different outcomes?
There still remain massive opportunities to bridge the digital, physical and non-human identity ecosystems from account creation to age verification to cloud authorization to credentialing and beyond. From an investor standpoint, the problem space has been outlandishly fertile for acquisitions and consolidation amongst players. This continues to incentivize founding teams to spawn new and innovative solutions.
—–
We at Lotus are incredibly excited by the tech that fuels Cybersecurity. If you are an investor, researcher, or founder in the space: reach out at ayla.j@thelotuscapital.com – I would love to chat with you.
______________________________
If you are a builder, investor or researcher in the space, I would love to have a chat – please reach out to me at amit.k@thelotuscapital.com